Stories about Threatened Voices from April, 2016
Xulhaz Mannan, an LGBT Activist in Bangladesh, Is the Latest Victim in a String of Brutal Killings
Since 2005, at least 23 bloggers and activists have been killed and scores of others attacked or threatened with death for their progressive and secular views.
Imprisoned Iranian Cartoonist Hadi Heidari Goes Free
"By the grace of God, I was released from Evin Prison tonight after serving time. Thank you all for the kindness," Hadi Heidari wrote on Instagram.
A University Professor Is Hacked to Death, Another Victim of Deadly Intolerance in Bangladesh
Rezaul Karim Siddique joins a long list of intellectuals, bloggers and foreigners who have lost their lives in similar killings purportedly carried out by Islamist militants.
Iranian Cartoonist Atena Farghadani's Prison Sentence Reduced From 12 Years to 18 Months
"To my cartooning colleagues around the world: let's keep watching and speaking out for Atena Farghadani."
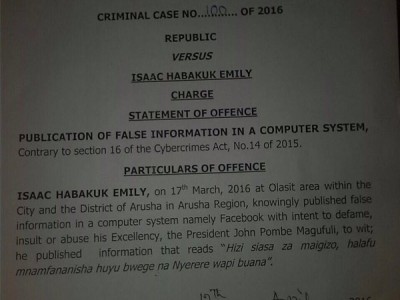
Tanzania's Cybercrime Act Makes It Dangerous to “Insult” the President on Facebook
Tanzanian netizen Isaac Habakuk Emily is accused of posting a controversial Facebook message "insulting" the president of Tanzania.
Iranian Blogger Struggles for Health and Freedom After 18 Days on Hunger Strike
Anti-censorship activist and blogger Hossein Ronaghi Maleki has been on hunger strike since March 26, and his health is deteriorating rapidly.
Netizen Report: US-Iran Tensions Rise Over Cyber Conflict, Human Rights
Death toll rises yet again for secular Bangladeshis, China scrubs #PanamaPapers from the Web and Egypt exploits two-step verification to target activists' online accounts.
Secular Activist Targeted and Killed in Bangladesh
The 28-year-old law student was murdered by three assailants in Dhaka, Bangladesh, on April 7, 2016. The young man was most likely targeted for his critiques of religious conservatism.
Two-Step Verification in Egypt: Strength or Weakness for Online Security?
Independent researchers in Egypt have identified what appears to be a new technical avenue for state surveillance: manipulation of the two-step verification process. Many activists, journalists and regular citizens throughout the world use two-step verification (see below) on social media and email services in order to bring a new layer...
Zambian Deputy Minister Attacks Bank Employee Over Facebook Comment
The Deputy Minister’s visit reportedly was marked with obnoxious name calling, threats and shouts that shocked clients and security personnel at the bank.
Posting Photos of Red Bowls on Facebook Is Now Deemed Seditious by the Thai Junta
"The Thai junta’s fears of a red plastic bowl show its intolerance of dissent has reached the point of absolute absurdity."