
ISIS threatens an attack in the UK in a video featuring a clip of David Cameron's speech expressing solidarity with France following the November 13 Paris Attacks.
The latest propaganda video from Daesh (also known as ISIS), entitled “Kill Them Wherever You Find Them” and released by Al-Hayat Media on January 24, claims to feature all those who participated in the November 13 Paris attacks.
Replete with gore, killings and threats of future attacks, it bore all the typical hallmarks of the brutal Al Qaeda offshoot that has taken over large territories in Iraq and Syria. But one thing stood apart in this video: it included what it describes as an encrypted message about the group's next attack.
The video also features a supposedly decrypted email about the Paris attacks:

Screenshot from Daesh video, of an email supposedly sent using GPG email encryption software.
With only the video as evidence, it is impossible to determine whether or not the email is real, but the simplistic language and exclusive use of English cast doubt on its veracity.
Readers who use encrypted email will notice the peculiar use of the “Start of PGP/Inline encrypted data” followed by the word “Decryption”. This terminology is typical of encrypted email, but the particular order in which the words appear is not.
Edward Snowden, the whistleblower behind the leaks of global surveillance programs of countries such as the US and the UK, also pointed out that the setup of the encrypted email is fake:
Journos: The #ISIS video's “encrypted email” is confirmed fake. If any official responds as if it's real, push back. pic.twitter.com/fKHAAk1SAa
— Edward Snowden (@Snowden) January 24, 2016
Does #ISIS see advantage in West limiting access to strong security? Juxtaposing “spooky” fake crypto with anti-crypto Cameron implies yes.
— Edward Snowden (@Snowden) January 24, 2016
The OSINT, a Twitter account dedicated to “open source intelligence”, featured edited clips from the video explaining the group's use of encrypted email:
And ends with an encrypted email, not decryptable to the viewer, threatening London. pic.twitter.com/WBIq4UKqAh
— The OSINT (@theosint) January 24, 2016
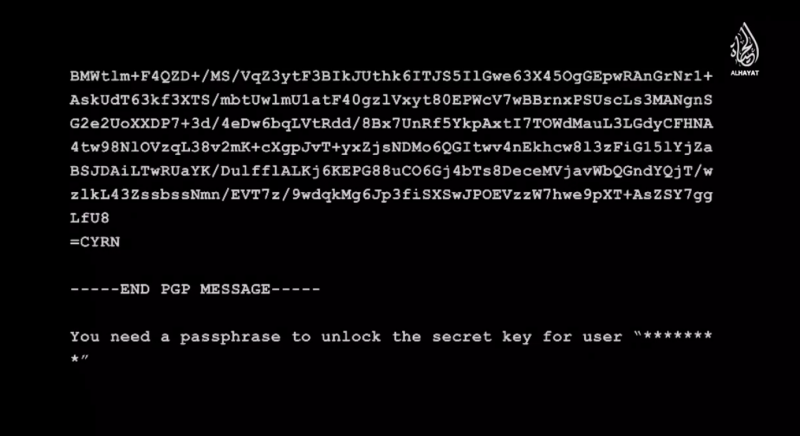
Screenshot of the supposedly encrypted email at the end of the video.
The communication strategies of the Paris attackers was up for much debate in the immediate aftermath of the attacks. Fears prevailed that law enforcement were not able to prevent such acts because of the use of encryption, propelling a new round global controversy that some are describing as a new phase in the crypto wars.
The attacks have become the latest scapegoat for those in support of expanding surveillance measures, despite evidence demonstrating that the Daesh members involved in communicating and coordinating the attacks were not using encryption. In fact, one of the phones of the attackers was recovered with an unencrypted SMS message communicated during the attack.
None of this has stopped western government efforts to more tightly regulate encryption technology. New draft legislation in the UK seeks to expand law enforcement surveillance capabilities. It includes explicit clauses that will require communications providers to provide data “in a legible form“. In practical terms, this would mean that technology companies would be required to build backdoors to all encrypted communication — and to open those doors when served with a warrant.
Lebanese technologist and blogger Nadim Kobeissi, who is best known for his leadership in developing encrypted chat app Cryptocat explains why encrypted technologies cannot support the kind of “backdoor” that governments like David Cameron's are asking for:
The call for backdoors is nothing new….I’ve had well-intentioned intelligence officers ask me informally, out of honest curiosity, why it is that I would refuse to insert backdoors. The issue is that cryptography depends on a set of mathematical relationships that cannot be subverted selectively. They either hold completely or not at all. It’s not something that we’re not smart enough to do; it’s something that’s mathematically impossible to do. I cannot backdoor software specifically to spy on jihadists without this backdoor applying to every single member of society relying on my software.
The OSINT points to the savvy way in which Daesh plays into this debate in the U.K. and fears over encryption by ending their video with an encrypted email after threatening the United Kingdom with a similar style of attack.
ISIS might want the UK to overreact and ban encryption. Fading away David Cameron to transition to a GPG encrypted email is meaningful.
— The OSINT (@theosint) January 24, 2016
There is little doubt that ISIS has been following the new cryptowar. Banning encryption will not prevent them from having it.
— The OSINT (@theosint) January 24, 2016
Indeed, Daesh seems to be playing directly into the sensitivities of many western countries. The Paris attacks included strategic maneuvers that seemed intended to exploit and further exacerbate fears about the dangers of refugees being potential terrorists.
The fake Syrian passport planted on a body of one of the slain Paris attackers was testament to this. There is no doubt that these encryption tools featured in this video play into the same strategy.
After trying to instigate refugee ban with Paris attack, ISIS now taunting Western govts about encryption. https://t.co/Ty6wZgq9CE
— Matthieu Aikins (@mattaikins) January 24, 2016
Perhaps Daesh enjoys watching this new round of “crypto wars” unfold as they pull at the levers of the power politics that, among other things, lead to infringements on civil liberties and public security.
Government efforts to access end-to-end encrypted communication in the hopes of defeating, or preventing attacks are shortsighted. Despite account closures and policing of platforms like Twitter against Daesh, the group still remains at large and capable of publicly relaying their propaganda and recruiting. As the Washington Post reported in December, the State Department's counter-messaging team has gone through three leaders within less than a year while commencing and discarding multiple strategies. Targeting encryption has become one of the ham-fisted efforts in lieu of the failures of other strategies to counter terrorism online.
Ars Technica editor Glyn Moody writes:
…the video's encrypted message, whatever it says, shows perfectly why neither banning nor breaking crypto will help in the slightest.
Indeed encryption has been a hot issue for governments since the Cold War, but the first Crypto War did not commence until the introduction of PGP (“Pretty Good Privacy”) in the early 1990s (for full history see OTI's history of the First Crypto War here). Technologists and advocates are now in the middle of the second crypto war following the push for strong encryption in reaction to the Snowden revelations.
While governments, including the UK and US have called for backdoors to encryption, advocates such as Global Voices Advocacy and EFF alongside Internet giants like Apple and Google have pushed back against the weakening of encryption. Even with current capabilities at the hands of US and other Five Eyes partners (see unecrypted text messages of Paris attackers) there are deep doubts about the legitimacy of mass surveillance as a viable counterterrorism strategy.
Encryption debates peddled by governments play into Daesh's strategies of keeping governments further away from defeating the organization both online and offline. As the fake encrypted emails in the video suggest, Daesh does not exist because of encryption, nor does encryption technology enable it to function as it does.




1 comment
The latest propaganda video from Daesh (also known as ISIS), entitled “Kill Them Wherever You Find Them